The Mozilla Foundation, the nonprofit organization behind the Firefox web browser, is expanding a campaign begun last year to help consumers buy safe, secure connected toys and mobile gadgets this holiday season.
Mozilla’s 2018 edition Privacy Not Included buyers’ guide offers an assessment of the privacy and security qualities of 70 products, ranging from connected teddy bears and smart speakers to game consoles and smart home gadgets.
Strong Consumer Interest
More than half the listed products failed to meet the minimum security standards Mozilla created in concert with Consumers International, a global consumer advocacy group, and the nonprofit Internet Society. The guide invites consumers to interact with a “creepy” rating scale.
Some of the failed products may not be the kinds of products consumers generally associate with being vulnerable to misuse of user data. The goal is to make consumers and Internet of Things vendors more aware of privacy safety with respect to connected toys and mobile gadgets.
Last year’s first shopping guide revealed strong consumer interest in the privacy and security of connected toys and smart home products. Some companies that sold products also were interested. This year’s guide took the lessons learned last year and put them to work to build a better guide, according to Mozilla.
The main problem with an approach like this is that the desire for privacy varies among users, and there is no way to show that in Mozilla’s buyers’ guide, according to Shea Drake, content strategist and tech expert with Business.org.
“There’s no comparison tool, table of factors, or even standards for what is considered creepy versus whether it is useful/cool enough to be worth the creep factor,” he told the E-Commerce Times. “Alexa is voted as one of the creepiest products, yet there are still over 40 million units sold.”
How It Works
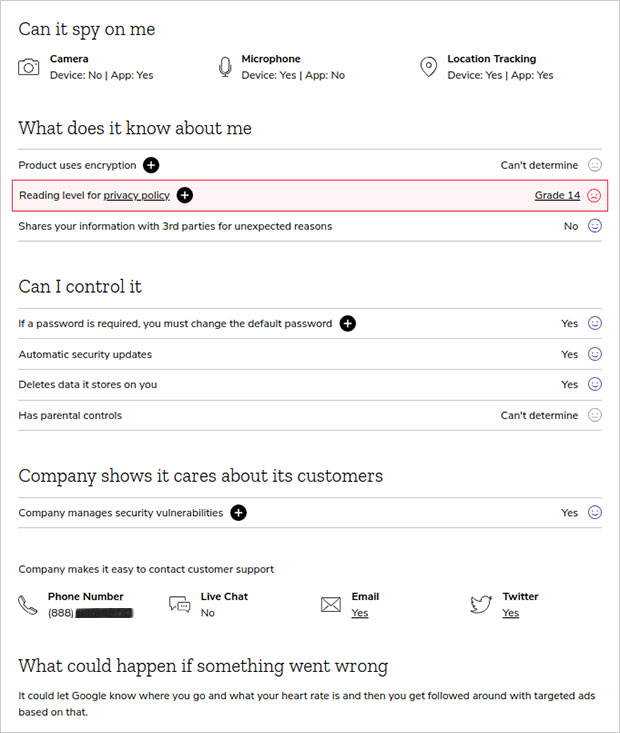
Consumers view pictures of the 70 products Mozilla included in the guide. At the top of the guide’s landing page is a horizontal row of pre-screened categories: Toys & Games, Smart Home, Entertainment, Wearables, Health & Exercise, Pets. Click on a product category to see the included toys or gadgets. Clicking on the image takes users to a product detail page where they can view the product’s characteristics.
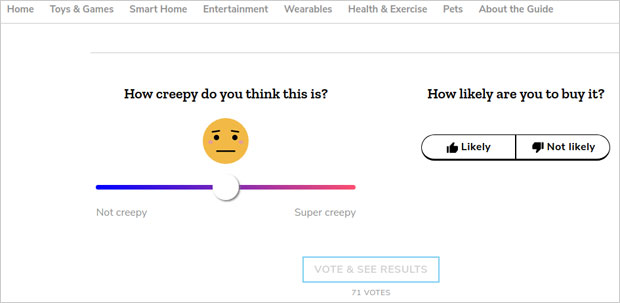
Consumers can rate products on a two-part Creep-O-Meter scale. A slider goes from “not creepy” all the way to “super creepy.” Respondents then can click on a thumbs up or thumbs down button to indicate their likelihood to buy the product.
Once a person votes, a display appears with a breakdown of the results, along with an opportunity to post and read other people’s comments on the product. Continue to scroll down the page to see a series of questions about the privacy characteristics of the product. The listings briefly explain what could happen if something should go wrong.
Mozilla includes a “Meets Our Minimum Security Standards” stamp on a page if the product has met its minimum security standards for IoT products.
Basic Safety Standards
Mozilla’s minimum privacy requirements highlight the fundamental ways Internet-connected products can fail when it comes to protecting your data. Mozilla’s researchers have assessed whether each product uses encryption, how easy the privacy policy is to read, how security updates are handled, and whether the maker addresses security vulnerabilities.
Mozilla’s bare minimum standards will reject connected toys and gadgets under the following circumstances:
- Communications are not encrypted — Only the sender and the receiver should be able to access the information; there should be no eavesdropping.
- There are no security updates — A product must support automatic security updates by default. Otherwise, companies cannot fix vulnerabilities in a timely matter if at all.
- Weak passwords are permitted — Many products have default password such as “1-2-3.” Even worse, the passwords are printed on the box.
- There is no easy way to reach vendors — It is often difficult to get privacy and data protection details from vendors.
- The privacy policy is indecipherable — Details should not contain complicated security jargon or require an advanced reading level. Many consumers overlook opting out of data collection or learning how to delete their data. Many do not even know what data is being collected and sold.
Product Analysis
Only five of the 18 products listed on the Toys & Games page meet the minimum standards. They are Microsoft’s Xbox One, the Nintendo Switch, Sony PS4, the Harry Potter Kano Coding Kit, and the Amazon Fire Kids Edition.
Just six of the 18 wearables in the guide pass Mozilla’s minimum standards. Consistency within a manufacturer’s product line is not always a given. For instance, Apple AirPods failed, but the Apple Watch Series 4 passed.
In the smart home products category, most smart speakers have safety approval. These products include the Amazon Echo and Dot, Google Home, Apple HomePod, Sonos One and the Mycroft Mark 1.
Want a Nest-based smart home? Forget about it. None of the highlighted products have a safety approval from Mozilla.
Useful or Not
Mozilla’s approach to consumer education may not get the hoped-for results, but anything to build awareness helps, said David Ginsburg, vice president of marketing at Cavirin. Although typical consumers have a low chance of being breached, this awareness helps with their overall cyberposture — for example, proper home router and WiFi configuration, or securing their laptops.
“As with any buyers guide, do not let it lead to a false sense of security or fear,” he told the E-Commerce Times. “This is the case with all guides — Consumer Reports, Yelp, Trip Advisor. It is always the responsibility of the consumers to understand their individual risks versus rewards.”
It’s also likely that the vendors that received a “creepy” rating will take a look at product security and documentation.
“What is perfectly acceptable in one region may not be in another,” Ginsburg said.
These kinds of alerts are only as effective as the audience they are able to reach and who actually read them, noted Nathan Wenzler, senior director of cybersecurity at Moss Adams Cybersecurity Consulting Services.
Mozilla’s guide is definitely a necessary resource, and if anything, it needs to be expanded to include as many products as possible, he suggested.
“Even by their own admission, 70 products is a drop in the bucket in comparison to the number of IoT devices out there,” Wenzler told the E-Commerce Times. “It is a good start on Mozilla’s part, but there needs to be more of this kind of thing for a wider array of products that need to be made available to consumers in more ways.”
Standards Needed
Mandated government standards may become the ultimate solution to regulate privacy guarantees, but self-policing by the industries involved may be a better goal.
Standards could include plain speak about how data is used when it is gathered, and an easy way to opt out. If you are paying for a product, vendors should not make more money on how you use that product, suggested Business.org’s Drake.
“Breaches or improper use should include not only a minimum fine to the government, but also to each user of the product,” he said. “Right now, consequences are fairly minimal, but standards only work if we enforce them.”
A line needs to exist between safety and privacy, ghough one could say that certain security vulnerabilities could result in safety issues, noted Cavirin’s Ginsburg.
“A combination of IoT and privacy regulations (like CCPA) on the national level will probably make it through the new Congress,” he added.
Bare Minimum Goals
Encryption should be used wherever possible, to protect communication between the IoT device and anything it is connected to, as well as any data stored on the device itself, Moss Adams Cybersecurity’s Wenzler suggested.
Minimum standards should include requiring the default password to be changed and not allowing older, weaker connection protocols over wireless or Bluetooth, he said.
Many older security protocols have been broken over the years and could be compromised easily today, Wenzler pointed out.
As customers become more aware of the threats these devices can present, the more they will demand that security features be built into products, he added. That ultimately will be a far more effective way to get manufacturers to make security protocols a standard feature of whatever they produce.
























































Social Media
See all Social Media