Since the dawn of the Internet age, criminals have looked for ways to profit on unsuspecting people while they browse the Web. Viruses, malware and other schemes were invented to infect and infiltrate systems, both at the enterprise and consumer levels. One of the most successful forms of cybercrime is social engineering, also known as the con man of the Internet.
Social engineering actually covers a wide range of security threats, not just those in a digital context, but it’s usually associated with attacks like phishing, where the criminal is trying to steal information from a user. Knowing how to defend yourself from such threats is critical to keeping your online data safe.
Here’s a look at how social engineering techniques have evolved over time and what people and businesses need to do in the future to protect themselves.
Elements of an Attack
The foundation of any social engineering attack is trust. The criminal is seeking to gain your trust through nefarious methods in order to receive something, which could include access permissions, passwords, or physical access to a building or a piece of hardware.
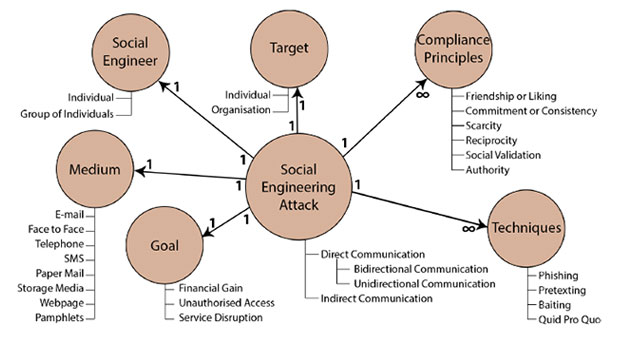
In most cases, social engineering attacks are carried out over the phone or online, so that criminals can disguise their true identities.
For example, you may have heard about scams where people receive multiple phone calls at home about a security issue with the Windows operating system. The attacker tries to gain enough trust to convince the target to provide a credit card number over the phone.
Online social engineering is more common because of how easy it is to perform in bulk. The best example is a widespread phishing scam. A hacker sends out a set of messages that try to mimic the look and feel of a bank or other company. The goal is to have Internet users click on rogue links and enter passwords or other sensitive information on a spoofed webpage.
New Forms of Social Engineering
Cybercriminals know that even the best scams will run out of steam eventually, which is exactly why they are constantly experimenting with new forms of social engineering. One growing trend is business email compromise (BEC). Attackers use phone and email messages together to impersonate a corporate executive and initiate fraudulent money transfers.
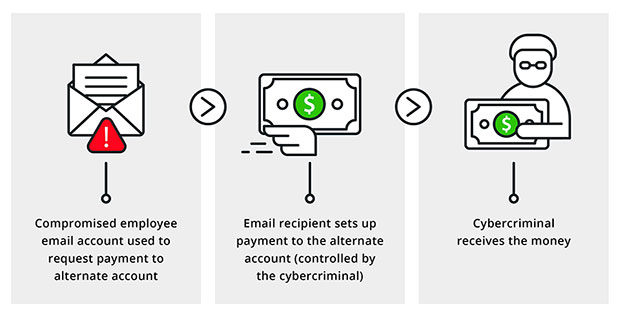
Individuals also need to be on the lookout for extortion scams. If you’re a victim of this type of attack, you’ll receive a message claiming that the sender has incriminating evidence about something you did in the past. These attacks often are targeted and will use real names and job histories.
Lastly, there’s catphishing which is a combination of an email phishing scam and a catfishing imposter. The attacker usually will claim to be a relative or lover of a person inside an organization and convince employees to provide sensitive information.
Training a Modern Workforce
Social engineering attacks are especially dangerous because all it takes is one weak link in an organization to initiate a damaging event. For example, if a server administrator falls victim to a phishing scam, that could leave a powerful password in the hands of a hacker, who then could execute a range of attacks across the network.
One mistake that a lot of companies make is to assume they should focus their cybersecurity efforts and budget on products like firewalls and intrusion detection systems. While these are indeed valuable, you cannot forget that the most vulnerable assets in your organization are the people working in it.
Cybersecurity awareness training should be a fundamental part of your company’s onboarding process. In addition, periodic mandatory sessions should be held every quarter with an emphasis on social engineering to ensure that your employees know what to watch for and how to protect themselves.
One part of the organization that people often forget about is the remote workforce. There’s a perception that if they are located outside of the network, their potential for damage is minimal.
The opposite is actually true. Although the best virtual private networks (VPNs) can protect you against hackers while you’re working remotely, they will not block social engineering attacks. For that reason, remote and traveling workers should be extra cautious when interacting with people over email or by phone.
Looking Ahead
Companies need to remain vigilant when it comes to cybersecurity, because social engineering is only going to get more sophisticated in the future. It’s only a matter of time before criminals start using artificial intelligence and machine learning algorithms to their benefit.
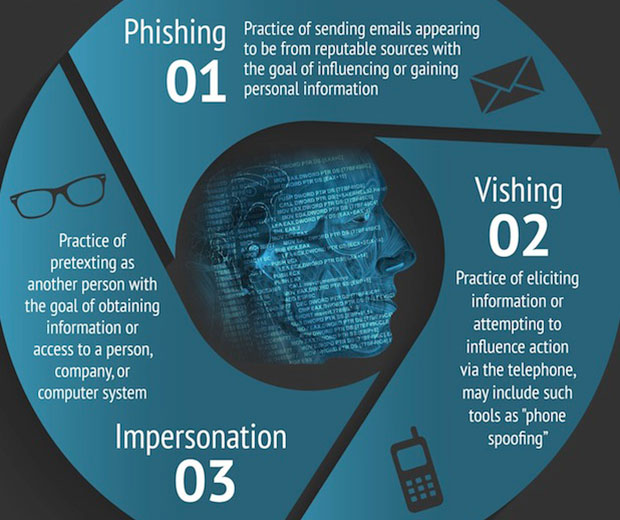
For example, a chatbot program could be used to imitate the writing style of a human in a live phishing scenario. Because it would be entirely machine-based, hackers would be able to execute this type of social engineering attack on a wider scale than ever before.
Or consider the advancements in voice simulation, which now allows for digital assistants to communicate with a user without any language barriers. This will make it easier for cybercriminals to impersonate different individuals and leverage those interactions for their benefit.
Final Thoughts
Most cybersecurity strategies are designed to handle straightforward scenarios. Firewall systems are built to receive a set of rules and then filter Web traffic based on those instructions. The same is true of malware scanners, which check parts of an operating system and look for dangerous code.
Where it gets really tricky is with attacks like social engineering, which introduce a human element that is hard to predict or control. You never know how an employee will react when targeted in a phishing or extortion scam. Even the best training programs won’t be able to look ahead to new forms of cyberattacks.
What’s important is that every enterprise remember that shoring up cybersecurity has to be an ongoing activity. You cannot simply throw money at it with a set of tools and trainings and assume your systems will be safe moving forward. Organizations have to stay up to date with best practices and make sure their employees do too.

















































Social Media
See all Social Media