Google on Thursday announced that its two years of collaboration withCWI, the Netherlands’ national research institute for mathematics and computer science, resulted in the launch of a successful attack against the SHA-1 cryptographic algorithm, a widely used standard protocol used to protect sensitive data in millions of computers.
The breakthrough research, led by Marc Stevens of CWI and Ellie Bursztein of Google, shows that the industry needs to send the SHA-1 standard into retirement, Google said, because the attack they were able to generate shows that the algorithm is no longer secure.
“Google has advocated the deprecation of SHA-1 for many years, particularly when it comes to signing TLS certificates,” Stevens, Bursztein and other team members noted in an online post. “As early as 2014, the Chrome team announced they would gradually phase out using SHA-1.”
Google urged the industry to switch to a more secure standard like SHA-256 or SHA-3.
SHA-1 is a cryptographic hash function used to underpin secure browser activity and manage code repositories, as well as for other security tasks on personal computers.
Hash functions are designed to compress large amounts of data into a message digest as a cryptographic requirement. However, attacks on the mathematical underpinnings of hash functions or increases in computational power can cause the requirement to fail over time, according to the researchers.
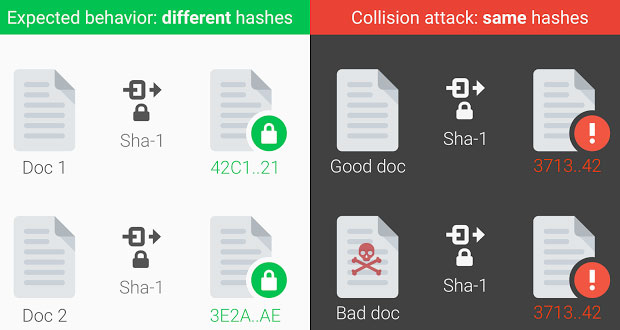
Collision Origin Story
Stevens in 2013 published a paper that outlined a theoretical approach to create an SHA-1 collision. The researchers went about creating a PDF prefix, which allowed them to create two documents with arbitrary but distinct visual contacts. Under this circumstance, they would hash to the same SHA-1 digest.
The researchers leveraged the company’s cloud infrastructure and technical expertise to create one of the largest computations ever completed.
Nine quintillion SHA-1 computations were completed in total, 6,500 years of CPU computation went into completing the first attack phase, and 110 years of GPU computation were needed to complete the second phase, Stevens, Bursztein, et al reported.
Despite the large calculations required, the attack was still 100,000 times faster than a brute force attack, which remains impractical.
Based on its vulnerability disclosure policy, Google committed to waiting 90 days before releasing the code that would allow anyone to create a pair of PDFs that could hash to the same SHA-1 sum. The company has also taken steps to detect the PDF collision technique in order to protect Gmail and GSuite users.
Google is also providing a free detection system to the public.
Phasing Out SHA-1
The real-world vulnerability means that anyone running an older computer system may be at risk, said Mark Nunnikhoven, vice president of cloud research at Trend Micro.
“The practical implications are that some older systems — seven years or more — that may still use the SHA-1 for digital signatures, survey verification or file comparison may be vulnerable to this attack,” he told the E-Commerce Times. “The reality is that very few systems should be exposed at this point.”
NIST, the standards board that regulates computer security, officially deprecated SHA-1 in 2011, Nunnikhoven noted, adding that modern systems have moved away from the algorithm.
The research essentially shows that the SHA-1 algorithm can be forged and must be replaced with something more secure, said Kevin Epstein, vice president of the threat operations center at Proofpoint.
“From a cybersecurity standpoint, this announcement reiterates the need for behavioral analysis as well as static analysis of code — for example, running an email attachment in a safe environment first and observing its behavior before letting a user open it, rather than solely relying on the digital signature for validity,” a Microsoft spokesperson said in a statement provided to the E-Commerce Times by company rep Rachel Martinez.
“Today’s report is further evidence that SHA-1’s useful lifetime has ended as part of the normal lifecycle of encryption technologies,” the spokesperson added. “Microsoft has worked with the industry since 2012 to phase out the use of SHA-1. Microsoft Edge and IE 11 do not consider websites using SHA-1 certificates secure, so do not show the lock icon that’s used to indicate a secure site in the browser’s address bar.”













































Social Media
See all Social Media