Zoom gave its users a big security upgrade Monday when it rolled out end-to-end encryption for its online meetings network.
E2EE puts control of the keys for scrambling data in the hands of meeting organizers. Before the E2EE rollout, encryption was done on Zoom’s servers, where someone with access to those servers could intercept the data.
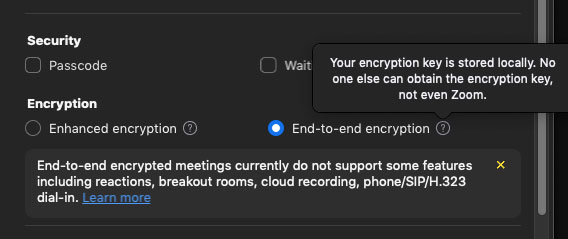
To use the new feature, customers must enable E2EE meetings at the account level and opt-in to E2EE on a per-meeting basis.
“Distributing keys to the clients and decentralizing trust gives users increased assurance that their communications are less likely to be intercepted through compromised keys or infrastructure,” Jack Mannino, CEO of nVisium, an applications security provider in Herndon, Va., told TechNewsWorld
Without end-to-end encryption, there’s a possibility that someone with access to the platform could intercept conversations, explained Dan Nadir, chief product officer at Theta Lake, a security and compliance solutions provider for collaboration platforms in Santa Barbara, Calif.
“That could be an unscrupulous employee, or someone who is able to breach the system,” he told TechNewsWorld. “Full end-to-end encryption eliminates this potential point of vulnerability.”
Oblivious Servers
In typical meetings, Zoom explained in a statement, its cloud meeting servers generates encryption keys for every meeting and distributes them to meeting participants using Zoom clients as they join.
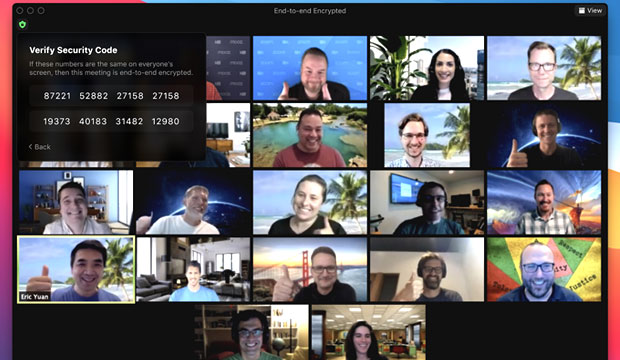
With Zoom’s new E2EE, it continued, the meeting’s host generates encryption keys and uses public key cryptography to distribute these keys to the other meeting participants, who will also see the meeting leader’s security code that they can use to verify the secure connection. The host can read this code out loud, and all participants can check that their clients display the same code.
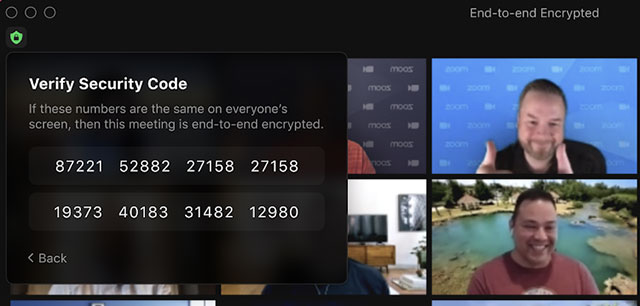
Zoom’s servers become oblivious relays and never see the encryption keys required to decrypt the meeting contents, it elaborated. Encrypted data relayed through Zoom’s servers is indecipherable by Zoom, since Zoom’s servers do not have the necessary decryption key.
“We’re very proud to bring Zoom’s new end-to-end encryption to Zoom users globally today,” Zoom CISO Jason Lee said in a statement.
“This has been a highly requested feature from our customers, and we’re excited to make this a reality,” he added.
Defusing Zoom Bombing
When used correctly, E2EE can make it difficult for even the best-resourced intelligence agencies in the world to eavesdrop on communication using it, observed Tod Beardsley, director of research at Rapid 7, a data and analytics security solutions provider in Boston.
“That’s why it’s such a powerful mechanism for ensuring privacy for the kinds of people who need to worry about intelligence organizations — journalists who are protecting sources, whistleblowers, civil rights activists, and others,” he told TechNewsWorld.
“The benefit for users, especially in COVID times, is substantial,” added Dirk Schrader, global vice president of New Net Technologies, a Naples, Fla.-based provider of IT security and compliance software.
“That’s particularly true for free users,” he told TechNewsWorld. “Around the globe many schools and volunteer organizations have been using Zoom to keep in touch, amid concerns about privacy and security.”
One of the early problems faced by users of the platform was “Zoom Bombing,” where intruders invaded meetings and disrupted them. “E2EE can stop that,” noted Chris Carter, CEO of Approyo, an SAP services provider in Muskego, Wis.
“No one can enter a conference before the host,” he told TechNewsWorld. “Anyone entering an E2EE conference has to provide information about themselves, and the host has to approve them. They can’t enter as an anonymous guest.”
Concern About Crime
Carter added that there were tradeoffs for using Zoom’s E2EE feature. “If you have E2EE on, you can’t record meetings to Zoom’s servers,” he explained. “You can’t do private chats or breakout rooms.”
Although E2EE is being offered to both free and paying users of Zoom, the company initially proposed limiting the feature to paying users over concerns the technology might be abused by criminals. That potential still exists.
“As platform services move to end-to-end encryption, it means that there is less opportunity for service providers and law enforcement to detect criminals and people using a service for malicious purposes,” said William Dixon, head of cybersecurity for the World Economic Forum, an international organization for public-private cooperation, headquartered in Geneva, Switzerland.
What that means, he continued, is people are having to innovate and evolve their thinking on detecting crime on these platforms. “Technology firms have been using a variety of techniques to detect malicious activity,” he told TechNewsWorld. “They’re investing heavily in analysis at the metadata level and of user analytics to provide tips to law enforcement of potential suspicious activity.”
While adding E2EE is a boon for Zoom users, the company is also benefiting from the move. “It brings them up to a level of security that a Microsoft typically has,” Carter maintained.
“Basically Zoom had no choice,” said Schrader. “Adding E2EE encryption to its services was a must after all the turmoil it went through.”
Nadir asserted that end-to-end encryption is table stakes for any company that wants to provide a serious solution for virtually any use case.
“Since it is table stakes for communications platforms, not having it is definitely a competitive disadvantage for any technology in the marketplace,” he added.
Single Sign-on On Horizon
The new encryption feature is available to both free and paid users and on Mac and PC desktop version 5.4.0 of Zoom, as well as the Android edition of the app and Zoom Rooms.
It uses the same 256-bit AES-GCM encryption used to secure non-E2EE meetings.
Zoom is calling this initial rollout of E2EE a “technical preview.” it hopes to gather input from customers on their experiences with the feature and encourages customers to enable Feedback to Zoom on their accounts and use it to comment on the new feature.
Zoom noted that this is just the beginning phase of E2EE for it. The next phase will include better identity management and single sign-on.
“Identity management and single sign-on support will make it easier for enterprise customers to use Zoom as a collaboration platform. It will reduce friction for end users,” Jeff Pollard, a vice president and principal analyst at Forrester Research, told TechNewsWorld
“This functionality augments and completes E2EE,” added Schrader.
“By misusing a stolen identity, an attacker can join an encrypted session impersonating the real identity to gather real-time information,” he explained. “These methods are not unique to Zoom, they are common for all kinds of services.”
“Still,” he continued, “Zoom adding this means it is taking security and privacy really seriously and wants to close all gaps.”